As a majority of you already know, last week’s ISC West was a big success with over 30,000+ security professionals making their way to the Sands Expo for a look at the latest security trends and technology. UniKey was lucky enough to have a few members of our Senior Leadership team attend the show and come back with some insights on the trade show. We sat down with, Roy Johnson, our VP of Strategic Accounts to hear his thoughts.
What trends stuck out to you?
Roy: The idea of the mobile credential is starting to mature and gain adoption. There was a lot of interest in the technology last year but this year we’re seeing a shift in adoption beyond just the early adopters and first movers. This is starting with crossover reader products that can process both mobile and legacy card credentials. I expect us to quickly see a shift to readers that abandon legacy card technology entirely.
How can these trends be applied to UniKey’s platform?
Roy: These trends are at the center of what UniKey does, clearly. However, what sets us apart is that our platform and IP portfolio were built from the ground up to achieve a user experience that is more convenient than a standard access card or fob. To truly realize proliferation of the mobile credential it has to be better than what we have now. In some cases, it’s way more complicated to use a mobile credential with some offerings than a standard card. Opening a door with your phone is interesting. Opening a door with a phone that you never have to interact with or remove from your pocket is actually easier and more convenient than standard cards.
What do you think the trends will be at next year’s ISC West?
Roy: We will see more collaboration and partnerships in the space. Keeping mobile apps up to date, managing complex backend server infrastructures and service level agreements is miles away from the core business expertise of most reader OEMs. Beyond that, the mobile credential really transcends the PACS industry in the long run. These credentials are being used to open the doors to homes, automobiles, hotels, and of course the office. The opportunities for innovation when all of these doors are connected and the data that provides from an ecosystem point of view is a game changer. That will be the foundation for truly intelligent and adaptive security that doesn’t inconvenience the people that should have access to an area while keeping others out.
What do you think differentiates UniKey from other companies you saw at the show?
Roy: Experience. UniKey is the largest mobile credential platform in the world with over 350,000 locks powered by us across 65 countries. We are experts when it comes to mobile credentials and the technologies surrounding them, it is our sole focus. More importantly, we recognize the immense value that our partners bring to the table in the form of manufacturing, distribution, and domain expertise for their vertical. When you work with UniKey to put a mobile credential in your product, you are working with a true partner. That is something we believe very strongly in.
Roy couldn’t have said it better. Working with our partners, Unikey aims to provide the very best in mobile access control solutions. To learn more about our platform and how you can work with us, visit unikey.com.
Next week thousands of security companies and experts will be making their way to Las Vegas’ Sands Expo for ISC West 2018. At last year’s ISC West all eyes were on video surveillance and biometrics, however, this year several different security technologies will compete for showgoers’ attention. Below, we have a list of just a few of the key access control technologies that will reign at this year’s show.
Internet of Things
The adoption rate for IoT technology has grown significantly since 2013 when it was reported to be an important factor for only 12% of organizations across all industries. Today that number stands at almost 30%. Industries, organizations, and entrepreneurs all over the world are finding ways to build on the IoT and its remarkable ecosystem in order to gain better insights on their customers that can help fine-tune unique customer experiences for each user. Additionally, IoT For All writes that when “your security measures are paired with IoT-enabled devices that bolster interconnectivity, you will have almost unlimited access to a digital trail of security events.” This kind of data holds the potential to give companies and users a better understanding of who and when individuals are accessing connected entry-points; giving them more control over their system. With that being said, security professionals can expect quite a few ISC sessions that will delve more into how the industry can utilize IoT and cloud-based access control solutions in order to create smarter, more intuitive products and more productive office spaces.
Biometrics
This year, biometrics will be making a reappearance at ISC West with many organizations showcasing facial recognition and fingerprint technology. However, this year’s biometric systems seem to be implementing more frameworks constructed on neural networks to boost the efficiency of visual data processing. As the name suggests, neural networks are more or less modeled after the human brain, and consist of “thousands or even millions of simple processing nodes that are densely interconnected.” Neural networks are also able to function in similar ways to the human brain, in that they’re able to process information in a similar fashion; something that can be used in object recognition systems such as facial or eye (retina and iris) recognition and even signature verification.
Video Surveillance
Yet another piece of access control technology that’s no stranger to the ISC spotlight, video surveillance, is expected to be another major focal point of the show for the second year in a row. Video surveillance systems are getting smarter through the use of video analytics which utilize machine learning methods like deep learning, artificial intelligence, and cognitive learning (like neural networks) and as they get more sophisticated, they’re able to be stronger threat detectors and data gatherers. Erin Harrington of SSI adds that “today’s cameras can track and analyze motion, sound, colors and even temperatures. They can recognize people, packages, pets, fire and specific activities like falling and breathing.” With all of its capabilities, video surveillance is generating more interest from security experts because of its daily opportunity to gather and process a massive amount of rich visual data. In the future, this data could be used as a foundation for predictive security systems.
Mobile
The final piece of security technology that will be a must-see at this year’s ISC West is mobile key technology. Mobile credentials have been a hot topic of discussion ever since the release of the very first smart lock, the Kwikset Kevo. While mobile keys are arguably one of the most secure and convenient forms of credentials, they’re also one of the most versatile. Mobile access control technology can be applied to all of the above security trends, giving several organizations and their products the ability to enhance their key offerings and features. For instance, using a mobile connected surveillance system, users can keep an eye out for potential threats from any remote location. Coupling this with mobile keys and their remote locking and unlocking abilities you get a similar system to Amazon Key, and a more protected front door. Additionally, adding mobile access control to biometrics could give systems an added layer of security and additional functionality. Take Samsung Pass and Apple Pay’s Face ID for example, where users can securely pay and/or verify their identity with their eyes and face; creating a more seamless and secure cashout process. With mobile access control, a smarter, connected security ecosystem is within reach.
Meet with UniKey at ISC West 2018
As you prepare for ISC West, we encourage you to schedule a meeting with UniKey’s Founder and CEO, Phil Dumas, and our team to find out how UniKey’s leading mobile access control platform can work with your legacy products. To find out more, visit https://unikey.com/isc-west-2018.
Today, we’re releasing our very first podcast on the topic of Women in Tech. In honor of International Women’s Day, UniKey’s Marketing Coordinator, Sofia Burton, sat down with two incredible women in the tech industry to discuss their experiences, how they arrived at their current positions, and advice they have for future generations. For Connie Klimko and Dr. Sarah Holderness, the path to entering the tech industry was full of perseverance, hard work, and commitment. Both Connie and Sarah not only work to exemplify the positive effects a woman can have on this maturing industry, but also the impact that diversity, as a whole, can have on an organization. To hear more about what motivated these women to be a part of the tech industry, check out the podcast below.
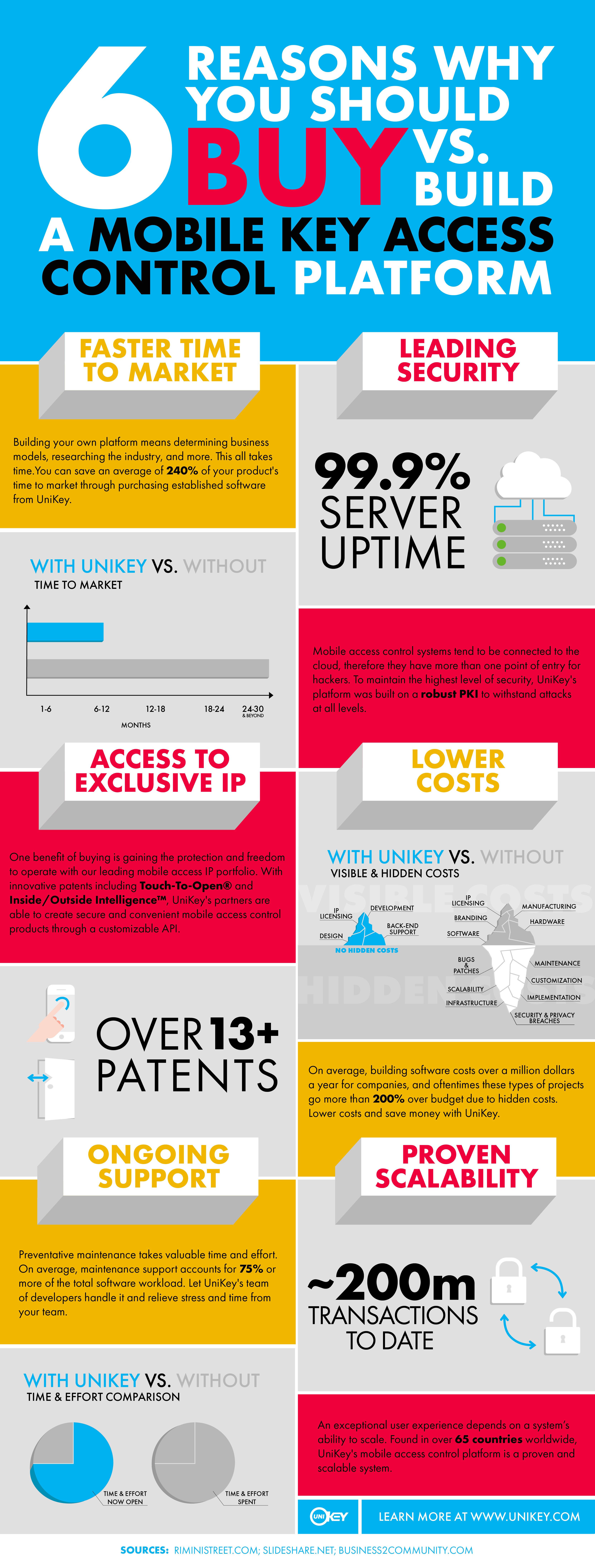
When you’re looking to integrate mobile access control solutions into your legacy PACS products, you want to do your homework before choosing the right system and partner. The primary focus for any valuable mobile access control supplier should always be on their diligent implementation of the latest security standards and methods of encryption. However, there are several other concerns and questions your company should evaluate before choosing a supplier. For example: What transmission standard does the supplier utilize? What advantages come with partnering with the supplier? How many companies and end-users have they served? What are their plans for future technological growth? And how much support can your company anticipate from this company? The list goes on. Nevertheless, let’s begin with the first question.
Methods of Communication
Understanding and identifying a mobile access control supplier’s chosen communication protocol can help your company narrow down a long list of potential partners. For instance, if your company already uses Z-Wave then you will want to find a company that uses the same communication protocol. This will make the integration process smoother for both companies. Although, if your company is looking to take an additional step toward incorporating other connected devices that can communicate with your upcoming mobile access control product, such as thermostats, video surveillance, and voice assistants, then considering a more ubiquitous transmission may be the way to go. Eifeh Strom from ASMAG, adds that “protocols such as BLE and Wi-Fi are the most common and have the advantage of being universally available, as they are part of every computer and smartphone,” making further integrations more applicable to mobile access control solutions using these protocols.
Gaining the Competitive Advantage
In addition to determining the most advantageous transmission protocol for your mobile access control product, companies should also examine their mobile key partner’s technology. Choosing a partner that maintains a unique mobile access control system can help distinguish your product from your competitor’s as well as deliver better experiences to your end-users. Moreover, in order to save your company a huge headache, you’ll want to question all potential partners’ ability to deliver a proven, scalable system. Creating a secure and seamless environment for your customers will hinge on your mobile access control product’s ability to uphold security and functionality, whether it’s for 1 or 1,000,000+ users. Another hallmark of a sophisticated mobile access control system is its adaptability to future technology. A system that is designed with extensibility in mind will be the one to help keep your mobile access control product future-proof.
Don’t get locked In
Finally, a significant indicator of a valuable mobile key partner is their ability to comply with partners’ and end-users’ needs. Jim Romeo of SDM Magazine states that another good way to identify the right mobile key supplier is by looking at their partner system. A sign of a solid access control supplier is when your “customers do not feel locked into a proprietary system that limits their options and means they’re stuck with greater expenditures to stick with the system and its unique maintenance.” In short, look for partners that will allow your end-users the freedom to choose their credentials. Something as simple as offering key cards as well as mobile keys can ease the transition from RFID/ Magstripe cards to mobile credentials for your company’s end-users.
Choosing the right mobile access control partner can be a difficult and overwhelming process. The above points are just a fraction of what companies need to consider. To better aid in your company’s search for the right partner and solution, visit unikey.com.
It’s hard to believe that since we posted this article a little over a year ago, there has been such a high level of advancement and change throughout the automotive industry. Tesla, which seemed to be at the forefront of the self-driving vehicle industry is now sharing the spotlight with car manufacturers like GM, Ford, and Volvo, which have taken strides into the future of automotives and even public transportation.
According to Ars Technica, companies like Alphabet’s Waymo and GM are leading the way in autonomous vehicle solutions by collaborating in a time when it’s a necessity for car manufacturers and software developers to team up and shape the future of transportation. For example, as far as autonomous public transportation goes, Lyft has teamed up with Ford to pave the way to the future of autonomous ride-hailing and sharing. Ford has intentions to build and deliver new innovations in commercial transportation with specific concentration on delivery services and ride-hailing patrons. Another example is GM. Since its acquisition in 2016 of Cruise, a San Francisco based autonomous vehicle developer, they have been working toward creating fleets of driverless vehicles. By the end of 2019, GM is expected to release its very own autonomous taxi-service, utilizing its proprietary, electric-powered Chevrolet Bolt.
But what about the experience and security behind these future driverless services?
In our previous article, “Connected Cars: Digital Keys in the Autonomous Era” we addressed the need for additional technology that will enhance the user experience as well as enable monetary benefits for consumers. In addition to automotive and AV software companies like Waymo, Ford, and GM, there will also be more unexpected companies like Facebook coming in to provide consumers with entertainment. The social media company has entered the automotive scene by sponsoring an initiative called “the new mobility world” which is meant to unite “carmakers, tech companies, and startups in areas such as autonomous driving and electric cars”. As we approach the more pivotal years for connected and autonomous cars, more tech companies like Facebook and their technology will bleed into the auto industry to offer AV consumers unique, in-car experiences.
Meanwhile, access control software developers will also make their way into the industry as someone or something will have to securely authorize, lock and unlock driverless ride-sharing vehicles. Moreover, once these vehicles have become the conventional means of transportation, car rental companies will also need a way for their customers to be authenticated and granted access to their cars. What’s more, autonomous delivery services will also be in need of a sophisticated credential to confidently authorize and authenticate the transfer of goods to consumers.
Altogether, there’s still a lot to be done until we see and experience driverless cars that are comparable to the ones in our favorite Sci-Fi movies. However, with all the collaborations, initiatives, and advancements in vehicle technology, the future of transportation looks promising and incredibly convenient.
Imagine a world where you don’t have to do the typical “phone, keys, wallet” check every time you walk out the door. A world where access to your home, car, and office is all simplified. Your phone is now your key. With UniKey’s one-of-a-kind mobile key platform, access control is taking on a new appearance, where security and convenience are no longer mutually exclusive.
It’s not every day your boss asks you to attend a trade show, let alone the NAHB’s International Builders Show. This being my first time attending a large industry conference, I had no idea what to expect from IBS. I originally pictured a large room full of sawdust, discussions on home improvement, and keynotes on “How to Properly Hang Drywall”. However, I could not have been more wrong.
My first stop at the show was in the west hall of the Orange County Convention Center. This section of the show was jaw-droppingly impressive. Upon stepping into the hall, I was met by a beautiful waterfall-like display from LP Building Co. Following this were some more incredible booths by the likes of Google Home and Nest, which looked as though they were uprooted straight from the company’s California HQ. They were the first in the home automation booths I was drawn to, but they certainly were not the last.
As I made my way through the packed hall, I noticed that many companies at the showcase were exhibiting products that allowed for automation, and/or remote management. Honeywell, for instance, featured their automated home solutions which contained their own connected camera, security systems, integrated smart locks, and of course a connected thermostat. Andersen Windows and Doors was also showcasing their own proprietary system, Andersen Connect. The system is a new connected window and door line that allows users to remotely lock and unlock their units as well as send virtual keys to family and friends for simplified access.
After making my way over to the other half of the show floor, I came upon Samsung’s booth, where a large group of people were huddled around a row of refrigerators. I had seen bits and pieces of what a smart refrigerator could do thanks to the show, Silicon Valley, however the features I saw on Samsung’s smart refrigerator, Family Hub, were still mind blowing. This intelligent appliance appeared to be exactly as its name suggested: the perfect hub for family-living. With Family Hub’s built-in display, users can entertain their loved ones and guests through the unit’s Spotify and TV mirroring apps. They can also enjoy the convenience of having the ability to order groceries through Instacart or GrubHub, while also being able to maintain a whole list of recipes for those perfect family meals.
Overall, I was really surprised to see that nearly all of the booths I walked past had some form of connected product or home automation tools on display. Even the toilets on display at the TOTO booth were self-cleaning after every flush! The fact that almost every company was dipping their toes in the waters of connected technology, tells me that simplification and automation are the keys to an ideal home experience. Not only that, but the concept of making the most simple home appliances smart, is sure to give homes those added hints of luxury and grandeur. If you didn’t get a chance to attend this year’s International Builders Show, I encourage you to check it out in 2019. At next year’s show, I anticipate the appearance of automated lawn mowers, multifunctional, color-changing walls, and a host of other smart, self-sustaining products.
Mandee Myers, UniKey Marketing Coordinator
CES 1967 was a show of many “firsts”. For the first time, consumer electronics companies finally had a unique event to showcase their latest products. The booths residing in the main halls of the introductory showcase were adorned with up and coming names like “Panasonic”, “Motorola”, “LG”, and “Philips”. Meanwhile, several new lines of television units, record players, and telephones were surrounded by fascinated showgoers; anticipating the products’ release dates.
CES: The Place to Be
Since the debut of the very first Consumer Electronics Showcase, several companies have selected the event as the one and only place to unveil their products. To name a few, CES 1967 was where Philips introduced the first mini-cassette. In 1970, the very first VCR was presented by Sony. And in 1981, CES showgoers witnessed JVC (and Sony’s) release of the very first camcorder as well as the first CD player developed by another Sony collaboration with Philips.
In the following years, inventions such as the Nintendo Electronics System, Tablets, and HDTVs were presented. Within a decade, CES became the platform for “anyone who was anyone” in the consumer electronics market to present their highly awaited products. It was the annual event where showgoers flocked to see the next big thing in electronics, and where companies like Sony, Atari, and Toshiba held a large share of the show’s spotlight. Yet, fast forward a few decades to 2018 and one can see who really owns the show.
Today’s CES
Whether you’re physically attending this year’s CES, or watching the show’s live stream, anyone who’s keeping an eye on the event will notice the path the show and its exhibited technology are taking. Over time, CES has transformed from being a huge marketing opportunity, to being a spectacle inundated with consumer inspired experiences. Take the above pictures for example. While being mindful of the very fact that technology wasn’t what it is today, we can still pinpoint the differences between CES then and CES today. In the very beginning, the showcase was all about the companies and what they had to show their audience members. Whereas today, it’s all about the audience members and the experience a product can offer them.
Power to the Consumer
Of course, to think that CES is all about the consumers would be a bit of an oversight. It’s still very much about the exhibitors. However, the focus has shifted significantly away from the companies in favor of focusing on the showgoers; the consumers. Whether it’s become an industry standard for companies to concentrate more on consumer UX, or whether it’s today’s technology enabling greater consumer interactions with products, the spotlight is now on the consumers.
Companies spend much more time developing experiences like the tunnel of OLED TVs by LG, pictured above. Through this unique display, audience members were able to see the vivid colors and the product’s compelling HDR graphics, while most likely visualizing how the TV would look in their own living rooms.
Creating the Experience
At this year’s CES, the panels, conferences, and keynotes will also reflect the show’s latest direction. With an entire conference track dedicated to it, UX and the “connected consumer” is rapidly becoming a hot topic and major focal point in the tech industry. As more tools and gadgets come online and begin to communicate with one another, electronics manufacturers are looking for ways to create a more fluid and interactive encounter between several devices and one consumer.
At UniKey, UX and the pursuit of seamless, connected experiences has been a tenant of ours since day one. We’re happy to see that as more technology becomes connected, and more applications come online, the rest of the tech industry is beginning to be heavily motivated by their consumers’ experiences. To learn more about UniKey and its pursuit of the ultimate, connected user experience visit unikey.com
For UniKey Technologies, 2017 has been a momentous year full of expansion and collaboration. With several products coming to life this year and nearly a dozen scheduled to launch in 2018, the company is rapidly delivering secure mobile access control solutions all over the world. Additionally, the company has not only seen great developments externally but internally as well. Since the beginning of the year, UniKey has filled key roles on the executive team to support further expansion plans next year.
For the original disruptors and creators of the mobile key market, the year has also been one of substantial growth across several key verticals, which will define the company and its success in the upcoming years. Upon the establishment of several strategic partnerships, the organization continues its expansion in the Commercial space while also focusing on opportunities in the Automotive industry. To expand on UniKey’s 2017 goals and successes and gather more insight into future endeavors, we sat down with Phil Dumas, Founder and CEO, and Lee Odess, COO.
Q1: What was UniKey’s biggest goal in 2017?
PHIL: Enabling as many major lock and access control companies to go mobile.
LEE: Continuing our expansion into the Commercial market and building the products we put under contract in 2016.
Q2: What motivated UniKey to develop a more open platform this year?
PHIL: There was great market demand for more open solutions. We also wanted to offer our partners more interoperability, which in turn can offer their users a more seamless at-door experience.
Q3: What do you see being the most significant access control trend in 2018?
LEE: Real mobile credentials and Bluetooth enabled readers built and supplied by (and for) the PACS OEMs.
Q4: What is UniKey going to focus on in 2018?
PHIL: 2018 will be very much like 2017, we’ll continue to focus on working with lock manufacturers and access control companies in order to replace the physical keychain with mobile solutions.
LEE: In 2018, we’ll also focus on delivering products all over the world, and continue to deepen our roots in Residential and Commercial and focus on the Automotive industry.
Q5: How will UniKey distinguish itself from its competitors in 2018?
PHIL: We will continue to partner with market-leading companies with exceptional manufacturing, branding, and distribution to proliferate mobile key technology to the masses.
UniKey is moving fast and making technological advances throughout all key verticals. With every partnership, the original producers of the mobile key are working to deliver a better at-door experience for all; improving the security and convenience of our homes, offices, and cars. In 2018, we expect to see some extraordinary smart security solutions that will bring progress to the physical security world. To learn more about UniKey Technologies, visit unikey.com.